The ever-present threat landscape demands a focus on secure software delivery. While DevOps methodologies have revolutionized the development process through collaboration and automation, integrating security throughout the lifecycle remains paramount. This is precisely what DevSecOps practices achieve, as discussed in the article ‘DEVSECOPS VS DEVOPS: A COMPARATIVE GUIDE TO SECURE SOFTWARE DELIVERY.‘
This article explores DevSecOps tools, your secret weapon for building a secure and efficient software development lifecycle (SDLC). We’ll delve into how these tools can help you identify and address security weaknesses throughout the entire development process, from initial planning to deployment and maintenance. By leveraging DevSecOps tools, you can streamline development, minimize security risks, and ultimately build product your users can trust.
Understanding the SDLC and Security Vulnerabilities

Source: Freepik
The software development life cycle (SDLC) encompasses all the phases involved in creating product, from initial conception to deployment and ongoing maintenance. Security vulnerabilities are weaknesses or flaws within code, systems, or processes that malicious actors can exploit to gain unauthorized access, steal data, disrupt operations, or cause other damage.
Integrating security throughout the entire development lifecycle is crucial to minimize these vulnerabilities and build robust product. Here’s how security vulnerabilities pose risks at different stages of the SDLC:
- Planning and Requirements: Vague or incomplete security requirements can lead to vulnerabilities being built into the software from the very beginning.
- Design and Architecture: Poor system design or insecure architectural choices can create vulnerabilities that are difficult or expensive to fix later.
- Development and Coding: Coding errors, insecure coding practices, and unmanaged dependencies can introduce vulnerabilities into the codebase.
- Testing: Inadequate or incomplete testing can leave vulnerabilities undetected until the software is deployed in production.
- Deployment and Maintenance: Improper deployment configurations, outdated software, and a lack of ongoing vulnerability management can leave systems exposed to attacks.
By proactively pinpointing and addressing security risks throughout the SDLC, DevSecOps tools empower teams to build product that is more secure by design, reducing the risk of breaches, data leaks, and other security incidents.
Unveiling Security Weaknesses: A Multi-Pronged Approach

Source: Freepik
There’s no single silver bullet for uncovering hidden threats within your software. A comprehensive DevSecOps approach utilizes a multi-pronged strategy, employing various tools and techniques throughout the development lifecycle. Let’s delve into the world of Static Application Security Testing (SAST), a powerful technique that leverages static code analysis as its foundation.
SAST: Inspecting Code for Flaws without Execution
Static Application Security Testing (SAST) analyzes source code without actually executing the application. Imagine SAST tools as automated code inspectors, meticulously examining your codebase for potential security weaknesses, coding errors, and suspicious patterns. The core technology behind this inspection is static code analysis. Static code analysis techniques allow SAST practices to analyze the code itself, identifying these issues early in the development cycle. By proactively identifying vulnerabilities and coding errors, SAST empowers developers to fix them before they become bigger problems later. This proactive approach enables early detection and remediation of threats, leading to more robust product.
Benefits of SAST:
- Early Vulnerability Detection: SAST empowers developers to pinpoint security weaknesses early in the coding cycle. This proactive approach allows for swifter and more cost-effective remediation before these weaknesses evolve into bigger problems later in development.
- Improved Code Quality: By identifying coding errors and potential security weaknesses, SAST can contribute to overall code quality and maintainability.
- Reduced Security Risks: Proactive vulnerability identification and remediation lead to a reduced risk of security incidents, data leaks, and other security incidents.
- Faster Development: Early detection and remediation of threats can streamline the development process and lead to faster time to market.
Popular SAST Tools:
Here are some of the leading tools available in the market today:
- GitLab: GitLab offers a robust suite of development tools, including built-in SAST capabilities that can scan code for weaknesses and security misconfigurations.
- SonarQube: This popular open-source platform provides comprehensive code analysis, including SAST functionalities that identify security hotspots, code smells, and potential vulnerabilities.
- Snyk: Snyk offers a cloud-native application security platform with integrated SAST capabilities. It scans code for risks, open-source dependencies, and container image security issues.
- Codecov: This popular code coverage platform also offers SAST functionalities, providing developers with insights into potential security weaknesses alongside code coverage reports.
These are just a few examples, and the choice of SAST tool will depend on your specific needs and development environment. The important takeaway is that SAST plays a crucial role in DevSecOps by helping developers write safe code from the ground up.
Dynamic Application Security Testing (DAST): Simulating Attacks to Uncover Vulnerabilities

Source: Freepik
While SAST shines in scrutinizing code for weaknesses, it has limitations. Certain security gaps, like injection flaws or logic vulnerabilities, might not be readily apparent by simply analyzing static code. This is where Dynamic Application Security Testing (DAST) comes into play.
DAST: Simulating Real-World Attacks
Dynamic Application Security Testing (DAST) takes a different approach compared to SAST. Instead of analyzing code, DAST tools simulate real-world attacks on a running application. These tools mimic the behavior of malicious actors, probing the application for weaknesses and security threats. By simulating various attack vectors, DAST helps surface security issues that SAST might miss, providing a more comprehensive security assessment.
Benefits of DAST:
- Uncovers Runtime Vulnerabilities: DAST can identify threats that only become apparent when the application is running, such as injection flaws or logic vulnerabilities.
- Improved Security Posture: By simulating real-world attacks, DAST helps organizations identify and address vulnerabilities before they can be exploited by malicious actors.
- Compliance Requirements: DAST can be used to ensure compliance with industry regulations and security standards that mandate penetration testing.
Popular DAST Tools:
- Acunetix: Acunetix offers a comprehensive web application security scanner that can identify a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), and broken authentication.
- Burp Suite: Burp Suite is a popular open-source web application security testing platform that provides a wide range of features, including DAST functionalities for manual and automated testing.
- OWASP ZAP: OWASP ZAP is another popular open-source DAST tool from the Open Web Application Security Project (OWASP). It offers a user-friendly interface and extensive customization options for advanced users.
By combining SAST with DAST, DevSecOps teams gain a more comprehensive view of their application security posture. SAST helps discover exploitable flaws early in the development cycle, while DAST helps ensure that the deployed application is resilient against real-world attacks.
Beyond SAST & DAST: Expanding Your DevSecOps Toolkit (Security Tools)

Source: Freepik
While SAST and DAST are powerful tools, a robust DevSecOps approach requires a broader security net. Let’s explore some additional security tools that can be integrated into your DevSecOps workflow to address various security concerns:
1. Software Composition Analysis (SCA) Tools:
Modern software applications, including containerized ones, rely heavily on third-party libraries and open-source components. These components, while convenient, can introduce security issues if not managed properly. SCA tools address this challenge by:
- Vulnerability Scanning in Codebase: These tools meticulously examine your entire codebase, including dependencies used in container images, to detect security threats within these third-party libraries and open-source components.
- Outdated Library Detection: SCA tools also pinpoint outdated libraries and suggest updates, ensuring you leverage the most secure versions available.
- Improved Software Supply Chain Security: By proactively managing security issues within dependencies, SCA tools contribute to a more protected software supply chain.
Popular SCA Tools:
- Nexus Lifecycle
- Snyk
- WhiteSource
2. Securing the Containerized World: Vulnerability Management
Containerization has revolutionized application deployment, but it also introduces new security considerations. Container security practices are crucial for securing containerized environments. These practices often leverage specialized tools that:
- Scan Container Images: These container security tools scan container images for threats within the container itself, the operating system it runs on, and any configurations. They also incorporate SCA techniques to pinpoint security weaknesses within third-party dependencies included in the image.
- Ensure Security Throughout the Lifecycle: Vulnerability management practices, often supported by specialized tools, can be integrated throughout the container lifecycle, from image building to deployment and runtime. This ensures continuous security monitoring and helps identify and address security issues at any stage.
Popular Threat detection Tools (for Containers):
- Aqua Security (mentioned previously for SCA)
- Twistlock
- Anchore Engine
By using both SCA Tools and threat detection and response processes for containers, security teams can achieve a comprehensive security posture for your software development process. SCA tools safeguard your codebase against vulnerabilities within dependencies used across various projects, while vulnerability control secures the containerized environment itself.
3. Infrastructure Security Tools (Infrastructure Security, Cloud Security):
Securing the underlying infrastructure that supports your applications is crucial for a robust DevSecOps strategy. Infrastructure Security Tools provide visibility into your infrastructure security posture and help identify and address potential vulnerabilities. These tools can integrate with cloud platforms and infrastructure as code (IaC) to enforce best security measures throughout your infrastructure.
Popular Infrastructure Security Tools:
- Prisma Cloud
- AWS Security Hub
- Azure Security Center
4. Configuration Management Tools
Configuration management tools play a vital role in DevSecOps by automating infrastructure configuration and shifting security left across your environment. These tools ensure consistent security configurations across all systems, reducing the risk of human error and misconfigurations. Popular options include:
Popular Configuration Management Tools:
- Ansible
- Chef
- Puppet
By incorporating these additional security tools alongside SAST and DAST, security professionals can achieve a more robust security posture, addressing vulnerabilities across the entire SDLC and infrastructure.
Addressing Specific Needs: A Look at Specialized DevSecOps Tools
While SAST and DAST provide a solid foundation for DevSecOps security processes, specific needs often require specialized tools. Let’s delve deeper into how these tools can address your unique security concerns:
Shielding Your Codebase: Essential SCA Tools
Modern software development thrives on third-party libraries and open-source components. However, these dependencies can harbor security vulnerabilities if left unchecked. Software Composition Analysis (SCA) tools empower DevSecOps teams to proactively address this challenge.
SCA Tools: Guardians of Your Supply Chain
- Vulnerability Detection: SCA tools meticulously scan your codebase, identifying known vulnerabilities within third-party libraries and open-source components.
- Outdated Library Management: They pinpoint outdated libraries, suggesting updates to ensure you leverage the most secure versions.
- Weakness Tracking: Many SCA tools integrate with weakness control systems, allowing for vulnerability tracking, prioritization, and staying informed about emerging threats.
Popular SCA Solutions Compared (See Table Below)
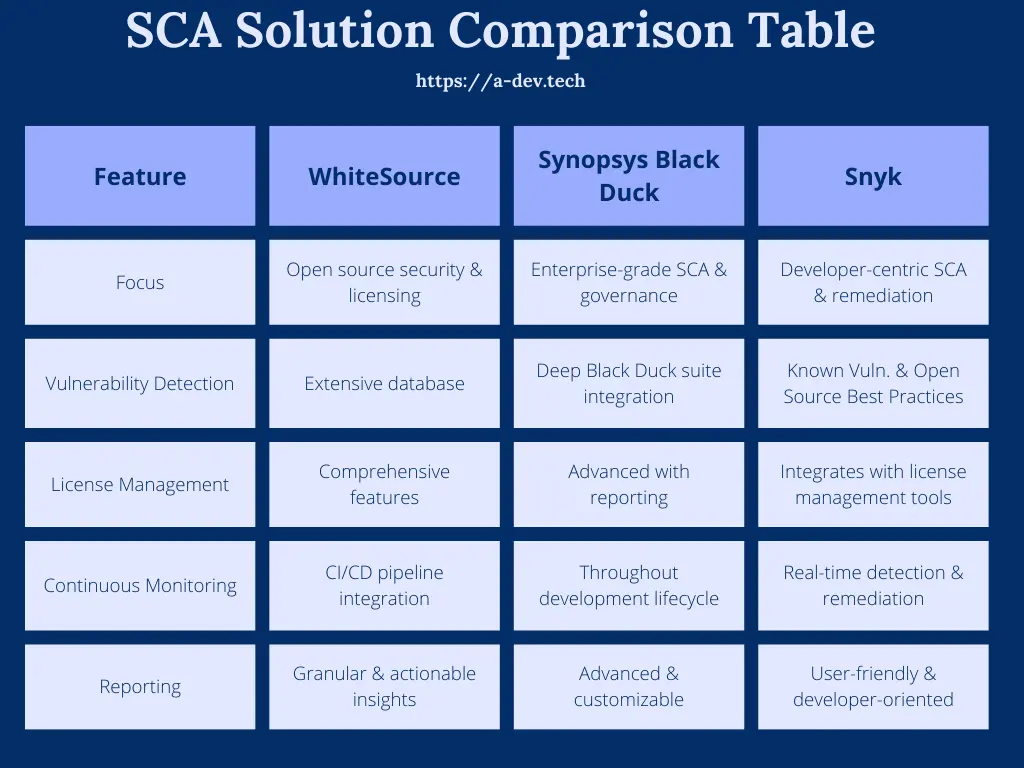
By incorporating SCA tools into your DevSecOps workflow,security professionals can proactively manage vulnerabilities within your software supply chain, mitigating risks associated with third-party dependencies.
Securing the Containerized World: Vulnerability Management for Containers

Source: Alexis Company
Containerization has revolutionized application deployment, but it also introduces new security considerations. Traditional security practices need to adapt to this new landscape.
Security hygiene practices for containers plays a critical role in securing your containerized environment. This approach utilizes specialized tools that offer functionalities like:
- Image Scanning: These tools meticulously examine container images, identifying vulnerabilities within the container itself, its operating system, and any configurations. Additionally, they leverage SCA (Software Composition Analysis) techniques to identify security vulnerabilities lurking within included third-party libraries or dependencies.
- Continuous Security Monitoring: Security risk mitigation strategies extend beyond initial image scanning. By integrating these practices throughout the container lifecycle (from image building to deployment and runtime), you achieve continuous security monitoring. This proactive approach helps identify and address vulnerabilities at any stage, significantly improving your overall security controls landscape.
Popular Security Hygiene Tools (for Containers):
- Aqua Security (previously mentioned for SCA)
- Twistlock
- Anchore Engine
By employing both SCA tools and security flaw remediation procedures specifically designed for containers, you can establish a comprehensive security strategy for your software development. SCA tools safeguard your codebase against vulnerabilities within dependencies used across various projects, while security flaw remediation procedures protects the container environment itself.
Fortifying the Foundation: Infrastructure Security Tools

The underlying infrastructure that supports your applications is a critical security frontier. Infrastructure Security Tools provide a comprehensive view of your security controls landscape by:
- Infrastructure Security Visibility: These tools offer visibility into your infrastructure security state, allowing you to identify potential vulnerabilities across your cloud environments, operating systems, and network configurations.
- Vulnerability Detection and Remediation: They can detect vulnerabilities within your infrastructure and often provide recommendations or automation for remediation efforts.
- Cloud Security Posture Management (CSPM): Many infrastructure solutions offer Cloud Security Posture Management (CSPM) capabilities, helping you continuously monitor and enforce security best practices across your cloud platforms.
By integrating infrastructure security solutions into your DevSecOps process, security teams can proactively identify and address vulnerabilities within your infrastructure, ensuring a robust foundation for your applications.
Enforcing Best Practices: Configuration Management Tools
Configuration management tools play a vital role in DevSecOps by automating infrastructure configuration and enforcing security best practices across your environment. Configuration Management Tools like:
- Ansible
- Chef
- Puppet
Popular Infrastructure Security Tools:
- Prisma Cloud
- AWS Security Hub
- Azure Security Center
Help you achieve consistent and secure configurations by:
- Infrastructure as Code (IaC): These tools enable you to define your infrastructure configuration as code (IaC), allowing for version control, collaboration, and automated deployment. This ensures consistent configurations across all systems.
- Enforcing Security Policies: Configuration management tools can be used to enforce security policies as code, ensuring all infrastructure elements adhere to pre-defined security standards. This reduces the risk of human error and misconfigurations.
By leveraging configuration management tools, you can streamline infrastructure management while simultaneously enforcing security best practices across your entire environment.
Choosing the Right DevSecOps Tools for Your Needs

Source: Freepik
Selecting the right DevSecOps tools is crucial for building a secure and efficient software development. There’s no one-size-fits-all solution, and the ideal toolset will depend on your specific needs and development environment. Here are some key factors to consider when making your choices:
Functionality:
- Align the functionalities of the tools with your specific security requirements. Do you need advanced DAST capabilities for complex web applications, or is a basic SAST solution sufficient?
- Consider the types of vulnerabilities each tool can identify and the level of granularity it offers.
Integrations:
- Seamless integration with your existing CI/CD pipeline is essential for smooth operation. Look for tools that offer native integrations or well-documented APIs for easy integration.
- Consider how the tool will fit into your development workflow. Will it disrupt existing processes, or can it be easily adopted by developers?
Ease of Use:
- The learning curve of the tool should be considered. Will your developers require extensive training, or is the tool intuitive and user-friendly?
- A user-friendly interface can encourage developer adoption and improve overall security awareness within the team.
Scalability:
- As your project grows and evolves, your DevSecOps tools should be able to scale accordingly. Choose a tool that can handle increasing code volume, application complexity, and growing teams.
- Consider if the tool can support your CI CD pipelines, integrating seamlessly into your automated build and deployment processes.
Pricing :
- DevSecOps tools come in a variety of pricing models, including open-source, freemium, and commercial options. Open-source tools can be a great starting point, offering valuable functionalities without initial licensing costs.
- Evaluate your budget and resource constraints when choosing between open-source and commercial options. Commercial instrumets often provide additional features, support, and scalability for larger enterprises.
By carefully considering these factors, you can make informed decisions about which DevSecOps tools will best suit your specific needs and development environment. Don’t hesitate to explore different options, leverage free trials, and involve your development team in the selection process to ensure a smooth and successful integration.
Conclusion: Building Secure Software with DevSecOps Tools
By strategically integrating DevSecOps tools throughout your software development lifecycle (SDLC), you can significantly reduce security vulnerabilities and build more robust software. These tools empower developers to proactively identify and address security weaknesses early in the development cycle, minimizing the risk of security incidents and costly remediation efforts later.
Key Benefits of DevSecOps Tools:
- Early Vulnerability Detection
- Improved Code Quality
- Reduced Security Risks
- Faster Development
- Enhanced Collaboration
Building a Secure Development Culture
DevSecOps tools are powerful allies in the quest for secure software, but they are just one piece of the puzzle. Building a secure development culture requires a holistic approach that includes:
- Security Awareness Training
- Security Champions
- Continuous Improvement
By combining DevSecOps tools with a strong security culture, security teams can create a development process that prioritizes security from the very beginning. This approach ultimately leads to building more secure software, protecting your organization’s data and reputation, and fostering trust with your users.
Looking Ahead: The Evolving DevSecOps Landscape
As highlighted by the ongoing emphasis on DevSecOps trends in 2024 (as discussed in the article “DEVSECOPS TRENDS 2024: BUILDING SECURE AND AGILE SOFTWARE DEVELOPMENT“), the focus remains on achieving a balance between robust security and agile development practices. New tools and methodologies are constantly emerging to address this critical need. Staying informed about these advancements and adapting your DevSecOps strategy accordingly will ensure your organization remains at the forefront of secure and efficient software development.