In today’s digital landscape, delivering secure software at speed is crucial. While DevOps revolutionized software delivery, it sometimes left security as an afterthought. This is where DevSecOps steps in. Strong DevOps teams are the cornerstone for successful DevSecOps implementation. For a detailed exploration of building high-performing DevOps teams in 2024, refer to an insightful resource: BUILDING HIGH-PERFORMING DEVOPS TEAMS IN 2024: ROLES, SKILLS, AND STRATEGIES FOR SEAMLESS EFFICIENCY AND SUCCESS. This blog post will delve into the core principles of DevSecOps, explore its benefits, and answer critical questions to help you decide if it’s the right approach for your organization.
What is DevSecOps?

DevSecOps is a cultural shift and a set of practices that emphasizes collaboration, communication, and shared responsibility for security between security, development and operations teams. It focuses on automating tasks and processes to deliver secure software faster and more reliably. Here are some key principles of DevSecOps:
- Shift Left Security: Security considerations are no longer relegated to the later stages of development. DevSecOps tools and techniques are introduced early in the SDLC to identify vulnerabilities in code and third-party libraries.
- Automation is Key: Repetitive security tasks are automated using DevSecOps tools. This includes vulnerability scanning, security testing, and compliance checks. Automation frees up time for security professionals to focus on strategic initiatives.
- Continuous Integration and Delivery (CI/CD): Security testing is integrated into CI/CD pipelines, ensuring that security issues are identified and addressed early and often. This helps to prevent security vulnerabilities from being deployed to production environments.
- Shared Responsibility: DevSecOps fosters a culture of shared responsibility for security. Software development and operations teams, as well as security professionals all work together to ensure the delivery of secure software.
To gain a deeper understanding of DevSecOps and its core principles, explore this comprehensive resource: DEVSECOPS TRENDS 2024: BUILDING SECURE AND AGILE SOFTWARE DEVELOPMENT.
DevSecOps vs DevOps: A Focus on Security Throughout the Pipeline
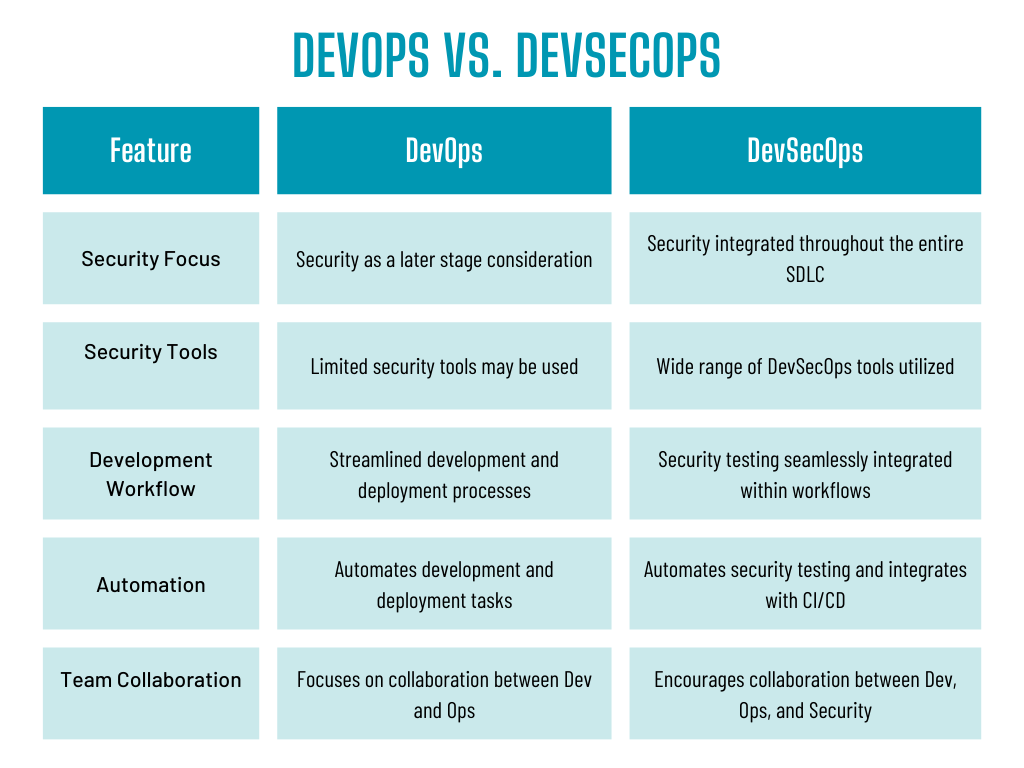
Here’s a breakdown of the key differences in focus between DevSecOps and DevOps when it comes to streamlining software development and delivery:
- DevSecOps vs DevOps: Security Philosophy: DevOps emphasizes collaboration, communication, and automation to deliver high-quality software faster. Security is often addressed later in the process, potentially leading to vulnerabilities. DevSecOps, on the other hand, integrates security throughout the entire SDLC (Software Development Lifecycle) from the very beginning. This “shift left” approach in security helps to proactively identify and address vulnerabilities early on, preventing them from becoming roadblocks later.
- DevSecOps vs DevOps: Tools and Techniques: DevOps utilizes tools and techniques primarily focused on automation and faster deployments. DevSecOps builds upon this foundation by incorporating additional security tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) to continuously identify and remediate vulnerabilities throughout the software development pipeline.
- DevSecOps vs DevOps: Development Workflow: While both methodologies emphasize efficient workflows, DevSecOps integrates security testing seamlessly within existing developer workflows. This means developers receive security feedback early and often, allowing them to fix vulnerabilities without significantly impacting development speed.
Choosing the Right Approach: DevOps vs. DevSecOps
While both DevOps and DevSecOps aim to streamline software development and delivery, they cater to different priorities within the process. Understanding these differences will help you choose the approach that best suits your organization’s needs.
DevOps: Speed and Efficiency First
DevOps prioritizes speed and efficiency, encouraging rapid software development cycles and faster software delivery. Key benefits include:
- Faster Delivery Times: Streamlined workflows and automation lead to quicker software releases, keeping your organization competitive and adaptable.
- Improved Developer Productivity: Clear communication, collaboration tools, and automated tasks free up developers’ time to focus on core coding activities.
- Increased Agility: DevOps practices enable organizations to respond to changing market demands with greater flexibility.
However, security considerations might be integrated later in the development lifecycle under DevOps. This can lead to vulnerabilities slipping through the cracks, requiring costly fixes later.
DevSecOps: Security Practices Throughout the Pipeline
DevSecOps builds upon the foundation of DevOps by integrating security practices throughout the entire Software Development Lifecycle (SDLC). It offers all the benefits of DevOps, but with a strong emphasis on security:
- Robust Security Posture: Proactive security testing and vulnerability identification throughout the development process minimizes the risk of security breaches.
- Reduced Risk of Security Breaches: Early detection and remediation of vulnerabilities prevent costly security incidents and reputational damage.
- Improved Software Quality: Security is no longer an afterthought, resulting in higher quality, more reliable software.
Making the Right Choice
The ideal approach depends on your specific needs and security posture. Here are some factors to consider:
- Security Sensitivity: If your software handles sensitive data or operates in a highly regulated industry, DevSecOps is the clear choice for a robust security posture.
- Development Speed: If speed to market is a critical priority and you have a mature security program in place, DevOps might be sufficient. However, even fast-paced environments can benefit from DevSecOps to avoid costly security delays down the road.
- Team Culture: A collaborative environment is essential for successful DevSecOps implementation. Teams need to be open to communication and willing to integrate security practices seamlessly within their workflows.
By understanding the focus of DevOps and DevSecOps, you can make an informed decision about which approach best balances speed and security processes within your software development process.
The next sections will explore the different categories of DevSecOps tools and Application Security Testing Methods (AST methods) used to identify and address vulnerabilities throughout the development process.
Implementing DevSecOps: A Step-by-Step Guide

Transitioning to a DevSecOps methodology requires careful planning and collaboration across development, security, and operations teams. Here’s a step-by-step guide to help you navigate the implementation process:
1. Assess Your Security Posture:
- Conduct a security risk assessment to understand your organization’s current security vulnerabilities and threats. This will help you identify areas where DevSecOps can have the most significant impact.
- Evaluate your existing development processes and tools to determine their compatibility with DevSecOps principles.
2. Define Your DevSecOps Goals:
- Clearly define your objectives for implementing DevSecOps. Do you aim to shorten development cycles, improve software security posture, or achieve regulatory compliance?
- Having well-defined goals ensures that your DevSecOps strategy is aligned with your overall business objectives.
3. Integrate DevSecOps with Existing Workflows:
- DevSecOps should seamlessly integrate with your existing development workflows to minimize disruption. Identify opportunities to introduce security testing and tools without significantly impacting development speed.
- This might involve integrating DevSecOps tools with your existing CI/CD pipeline for automated security checks throughout the development process.
4. Select the Right DevSecOps Tools:
- Choose DevSecOps tools that address your specific security needs and development environment.
- Consider factors like budget, ease of use, and scalability when selecting tools. Remember, the best approach is to adopt a combination of tools that cater to different aspects of security throughout the SDLC.
5. Foster Collaboration and Training:
- Successful DevSecOps implementation hinges on collaboration between development, operations and security teams.
- Invest in training programs to educate all teams on DevSecOps principles, best practices, and the functionalities of the chosen DevSecOps tools.
- Encourage open communication and collaboration to ensure everyone understands their roles and responsibilities within the DevSecOps process.
6. Establish Clear Communication Channels:
- Define clear communication channels to facilitate information sharing and problem-solving between teams.
- Regularly scheduled meetings or dedicated communication platforms can foster collaboration and ensure everyone is on the same page regarding security policies and development progress.
7. Monitor and Improve Continuously:
- DevSecOps is an ongoing process that requires continuous monitoring and improvement.
- Regularly evaluate the effectiveness of your DevSecOps pipeline and identify areas for improvement.
- Track key metrics like the number of vulnerabilities detected, time to resolution, and overall development speed to measure the success of your DevSecOps implementation.
8. Build a Culture of Security:
- DevSecOps goes beyond tools and automation. It’s about fostering a culture of security within your organization.
- Promote security awareness and encourage developers to take ownership of the security of their code.
- Recognize and reward security champions within your development teams to reinforce a security-conscious mindset.
By following these steps and fostering a collaborative environment, you can successfully implement DevSecOps and reap the benefits of secure, high-quality software development.
DevSecOps Tools: Your Security Arsenal

A wide range of DevSecOps tools empower you to address different security needs throughout the development process. Here are some categories to consider, along with some examples of open-source DevSecOps tools in each category:
- Static Code Analysis (SCA) Tools: These tools analyze source code to identify potential security vulnerabilities and coding errors without running the application.
- Example: Cppcheck (C/C++)
- Example: Bandit (Python)
- Software Composition Analysis (SCA) Tools: These tools scan for known vulnerabilities within third-party libraries used in your application.
- Example: OpenSSF Scorecard ( ogól noplace lang=”pl”>general-purpose)
- Example: Snyk (supports various languages)
- Static Application Security Testing (SAST) Tools: Similar to SCA tools, SAST analyzes source code for vulnerabilities based on predefined patterns and rules.
- Example: OWASP ZAP (supports various languages)
- Example: Flake8 (Python)
- Dynamic Application Security Testing (DAST) Tools: These tools simulate real-world attacks to uncover vulnerabilities during runtime, providing a more realistic view of application security posture.
- Example: OWASP ZAP (also offers DAST capabilities)
- Example: Netsparker Community Edition (limited features)
- Interactive Application Security Testing (IAST) Tools: IAST combines aspects of both SAST and DAST. It analyzes code and monitors runtime behavior for a comprehensive security assessment.
- Example: Burp Suite Community Edition (limited features)
- Example: DefectDojo (focuses on vulnerability management)
- Container Security Tools: These tools secure containerized environments used for application development and deployment.
- Example: Trivy
- Example: Clair (acquired by Docker)
- Cloud Security Posture Management (CSPM) Tools: For cloud-based deployments, CSPM tools provide continuous monitoring and management of your cloud security posture.
- Example: CloudSploit (free tier available)
- Example: Open Source Security Assessor (OpenVAS) (general vulnerability scanner)
- Compliance Management Tools: These tools help organizations automate compliance checks and ensure adherence to industry regulations and standards.
- Example: OpenSCAP
- Example: Anchore Engine (focuses on container security compliance)
- Security Orchestration, Automation, and Response (SOAR) Tools: SOAR tools automate security tasks and workflows, streamlining incident response and improving security efficiency.
- Example: Open XDR
- Example: Security Onion (focused on security monitoring and logs)
Remember: When selecting DevSecOps tools, consider factors like budget, ease of use, scalability, and your specific security needs. The best approach is often a combination of tools that cater to different aspects of security throughout each stage of the SDLC.
Uncovering Weaknesses: A Look at Application Security Testing (AST) Methods

In the DevSecOps world, proactive identification and remediation of security vulnerabilities are paramount. Here, Application Security Testing (AST) methods come into play. These techniques help developers uncover security weaknesses throughout the development lifecycle, ensuring a strong foundation for secure software. Let’s delve into some popular AST methods:
Static Application Security Testing (SAST):
- Function: SAST tools act like code auditors, meticulously examining source code without running the application. They scan for common coding errors, potential vulnerabilities based on predefined patterns, and security weaknesses.
- Benefits:
- Early Detection: Identifies vulnerabilities early in the development phase, saving time and resources compared to fixing them later.
- Efficiency: Analyzes large codebases quickly, making it ideal for continuous integration.
- Developer Integration: Can be seamlessly integrated into developer workflows, providing early feedback and promoting security awareness.
- Limitations:
- False Positives: May flag non-critical issues requiring manual verification.
- Runtime Blindspot: Limited ability to detect vulnerabilities that manifest during application execution.
Dynamic Application Security Testing (DAST):
- Function: DAST tools take a more dynamic approach. They simulate real-world attacks by sending malicious requests to a running application. This helps identify vulnerabilities that could be exploited by attackers, such as SQL injection or cross-site scripting (XSS).
- Benefits:
- Complements SAST: Detects vulnerabilities that SAST might miss, providing a more comprehensive security assessment.
- Realistic View: Offers a more realistic picture of your application’s security posture by mimicking real-world attack scenarios.
- Limitations:
- Resource-Intensive: Can be time-consuming to run thorough tests, especially for complex applications.
- Coverage Challenges: May not achieve complete code coverage, potentially missing certain vulnerabilities.
- False Positives: Similar to SAST, DAST can generate false positives that require investigation.
Interactive Application Security Testing (IAST):
- Function: IAST combines the strengths of both SAST and DAST. It analyzes source code for vulnerabilities (like SAST) and then monitors the application’s behavior during runtime (like DAST). This provides a more holistic view of application security.
- Benefits:
- Hybrid Power: Leverages the advantages of SAST (early detection) and DAST (runtime testing) for a comprehensive approach.
- Deeper Insights: Offers deeper analysis of runtime vulnerabilities, helping developers understand the root cause of security issues.
- Limitations:
- Complexity: Setting up and managing IAST can be more complex compared to SAST or DAST.
- Skillset Requirements: Effective utilization might require specialized skills for configuration and analysis.
Choosing the Right AST Method
The optimal AST method (or a combination) depends on your project’s specific needs. Here’s a quick guide:
- Early Development & Code Analysis: SAST is a great starting point for identifying potential vulnerabilities early in the coding process.
- Later Stages & Runtime Testing: DAST becomes valuable during later development stages when the application is functional and needs runtime security assessment.
- Complex Applications & Deep Analysis: IAST offers a comprehensive approach for complex applications requiring in-depth security analysis throughout the development lifecycle.
By incorporating these AST methods into your DevSecOps pipeline, you can proactively identify and address security vulnerabilities, ultimately building more secure and reliable software.
This improved section offers several enhancements:
Benefits of DevSecOps
Implementing DevSecOps offers a multitude of benefits for organizations:
- Improved Security Posture: By proactively identifying and addressing vulnerabilities, DevSecOps helps organizations build software with a stronger security foundation.
- Faster Time to Market: Automating security processes and integrating security testing within CI/CD pipelines streamlines the development process and reduces time to market.
- Reduced Costs: Early detection and remediation of security vulnerabilities is significantly cheaper than fixing them after deployment.
- Enhanced Compliance: DevSecOps helps organizations meet industry regulations and compliance standards more effectively.
- Increased Developer Productivity: Automating security tasks frees up developer time to focus on core development activities.
Is DevSecOps part of cybersecurity?
Absolutely! DevSecOps is an essential component of a comprehensive cybersecurity strategy. By proactively identifying and addressing security vulnerabilities throughout the SDLC, DevSecOps helps organizations build robust security postures and mitigate the risk of security breaches.
Does DevSecOps Require Coding?
While some DevSecOps tools require scripting knowledge, many tools are designed to be user-friendly and accessible to developers with varying skillsets. Additionally, DevSecOps emphasizes utilizing existing developer tools and integrating security testing seamlessly within existing workflows. Security professionals can also configure and manage many DevSecOps tools, minimizing the coding burden on developers.
Conclusion
DevSecOps is a powerful approach that empowers organizations to deliver secure software faster and more efficiently. By integrating security throughout the development lifecycle, DevSecOps fosters collaboration between security, development and operations teams. This collaborative approach ultimately leads to a more robust security posture, a competitive advantage in today’s digital world, and software built with user privacy in mind, which aligns perfectly with A-Dev’s commitment to protecting user data.
If you’re interested in learning more about DevSecOps practices that prioritize user privacy, A-Dev offers a wealth of resources (you can’t include a link here, but you can mention brochures, workshops, etc.). These resources can help you implement DevSecOps in a way that safeguards user privacy while building secure and reliable software.