
Handling health data in the cloud is a big deal. One misstep in HIPAA and you can get hit with huge fines, legal trouble and irreparable damage to your reputation. For DevOps and cloud teams, understanding HIPAA isn’t just about avoiding penalties – it’s about building secure, scalable systems that protect healthcare providers and patient information. This guide will walk you through the basics of HIPAA and give you practical steps to add data protection into your workflow.
What is HIPAA and Why Should DevOps and Cloud Teams Care?
The Health Insurance Portability and Accountability Act (HIPAA) is a US law that protects patient health information. If you’re working with health and human services, following these rules isn’t optional – it’s required to protect patient privacy. Whether you’re part of a DevOps team building health apps or doing cloud migrations for a health provider, knowing the basics can save your company from big fines and legal trouble.
HIPAA Terms Every DevOps Person Should Know
- Protected Health Information (PHI): Any personal health data that can identify someone, like medical records, names and contact info.
- Covered Entities: Hospitals, health insurers and healthcare clearinghouses that have to follow HIPAA rules.
- Business Associates: Third party vendors or service providers (like cloud providers and DevOps teams) that manage or process PHI for covered entities.
- HIPAA Privacy Rule: The rules for how PHI can be used and shared so individuals’ privacy is protected.
- HIPAA Security Rule: For ePHI, this rule requires technical and administrative controls to secure data.
- Breach Notification Rule: Notify individuals if their PHI is exposed.
HIPAA and Cloud Migrations for Healthcare
When it comes to cloud migrations for healthcare systems,HIPAA is at the top of the list. If you’re moving data or building a cloud solution for a hospital, you need to meet HIPAA requirements or face big penalties and data breaches.
Cloud Security Features for HIPAA
Major cloud providers like AWS, Azure and GCP have many cloud security features to help you comply with HIPAA. For example, AWS Shield has advanced DDoS protection which is critical for healthcare where uptime is life or death for patient care. Azure Security Center has centralized management for security and compliance policies, automating much of the monitoring and alerting required by HIPAA.
HIPAA Compliance in Cloud Migrations
The technical side of a cloud migration is important but, in health care, compliance is just as critical. When you’re dealing with personal health information (PHI) you must keep it protected. Whether it’s a social security number, phone number or medical records the sensitive nature of this data means cloud migrations have to be managed carefully. It’s not just about moving data it’s about understanding healthcare systems, regulations and the right security to keep everything in compliance.
HIPAA Breach Notification Rule
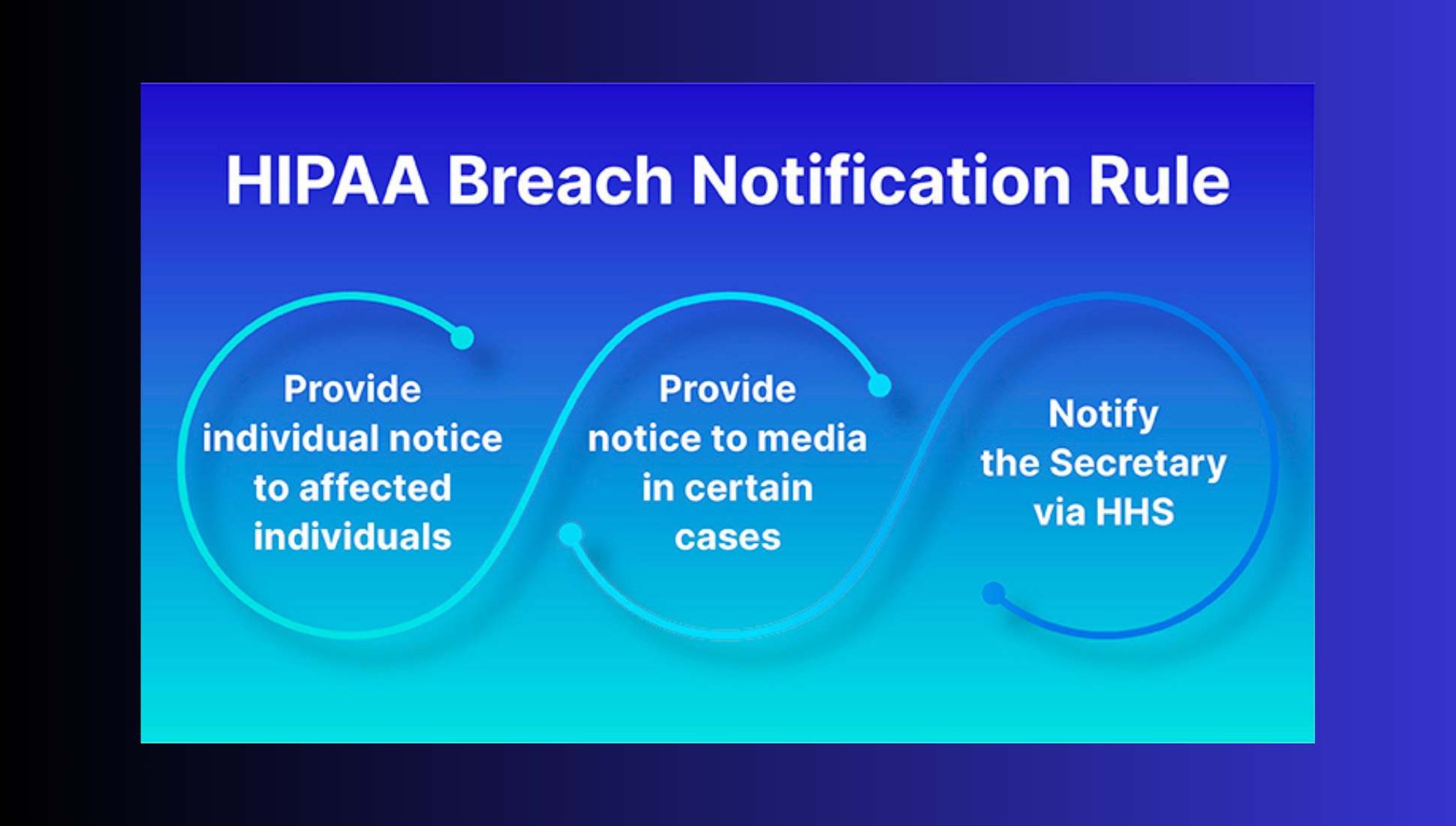
If there’s a security breach during migration you need to know what to do. HIPAA’s Breach Notification Rule requires you to notify affected individuals if their PHI is exposed. Whether it’s a patient or their family or spouse when necessary they need to be notified immediately. You need to have a plan in place to handle these situations quickly and securely to minimize damage to patient trust and privacy.
Data Privacy and Business Associates
When working with health data healthcare providers, insurers and their business associates all have a shared responsibility to keep patient information secure. If a third party vendor (like a cloud provider or DevOps team) is handling PHI they need to sign a Business Associate Agreement (BAA). This agreement makes it clear they understand the privacy and security requirements of HIPAA. Without this there’s a real risk of non-compliance which can lead to penalties and data exposure.
Health Insurance Portability and Cloud Migrations
A key part of HIPAA is portability of health insurance which means individuals retain their health insurance coverage when they change employers or plans. During cloud migrations this becomes a big concern. Health insurance information must be kept secure throughout the process so it’s portable and accessible when needed. That means strong encryption, access controls and solid security is non negotiable.
Make HIPAA Part of Your Cloud Strategy
In summary, HIPAA rules touch every stage of the cloud migration process from planning to execution. By making HIPAA part of your cloud strategy you ensure patient data is kept secure and confidential throughout the migration. Compliance tools like automated configuration checks and continuous auditing can make this process much easier and keep you on top of security threats as they evolve.
HIPAA Best Practices for DevOps: Granting Protected Health Information
HIPAA requires ongoing training for anyone handling PHI. Even if you’re not a healthcare professional, your team needs to know the rules. Security is everyone’s responsibility and an informed DevOps team is the first line of defense against compliance failures.
Technical Guidance for HIPAA Compliance in DevOps and Cloud Teams
Working with patient information in the cloud requires specific technical steps to be HIPAA compliant. Here are the technical steps for DevOps and cloud teams to configure encryption, automate compliance checks and implement RBAC in AWS, Azure and GCP.
Configuring Encryption for PHI in AWS, Azure, and GCP
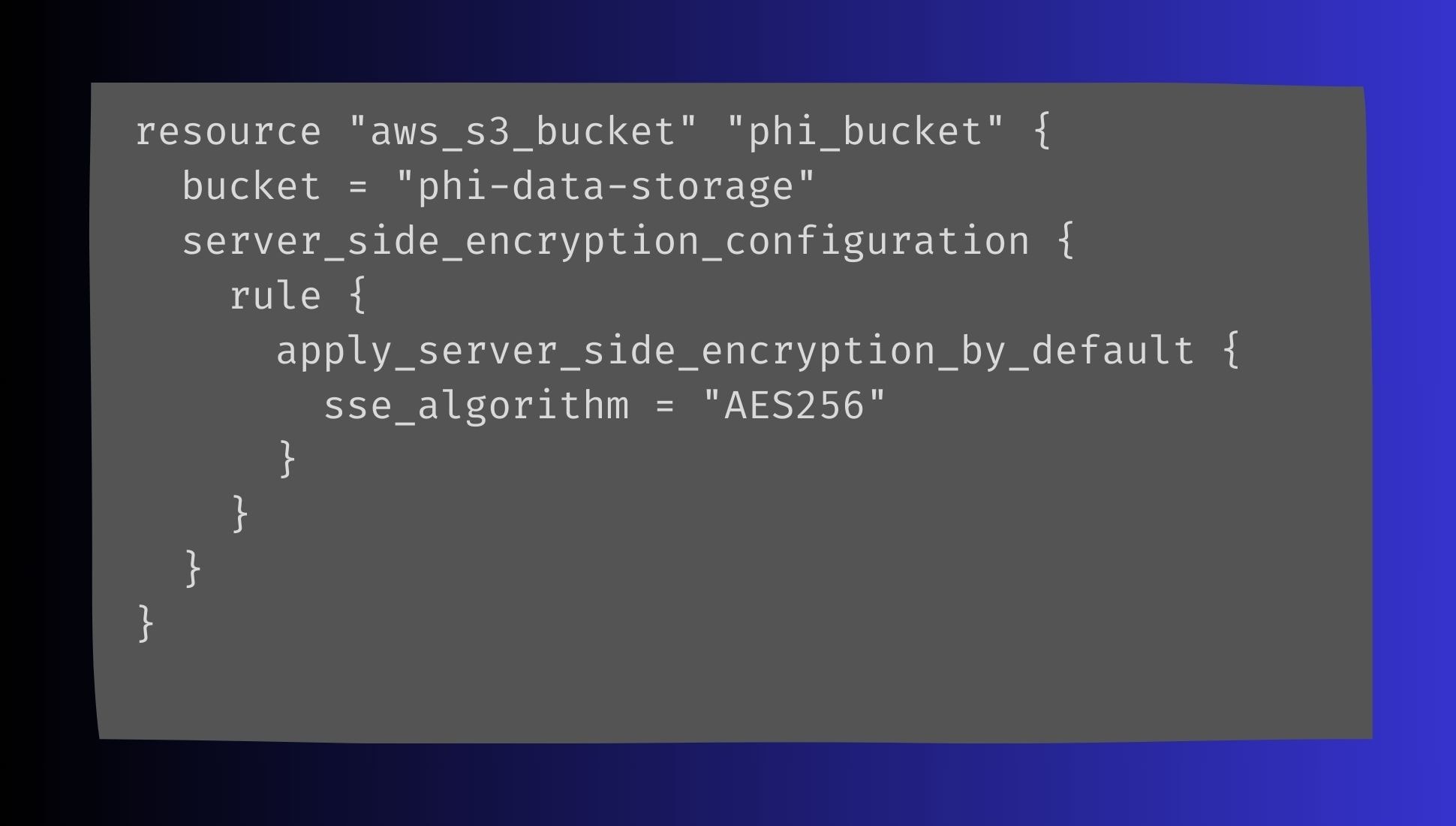
AWS Encryption for PHI: In AWS, use AWS Key Management Service (KMS) to manage encryption keys for PHI data. Here’s an example of how to enable server-side encryption for an S3 bucket using Terraform:
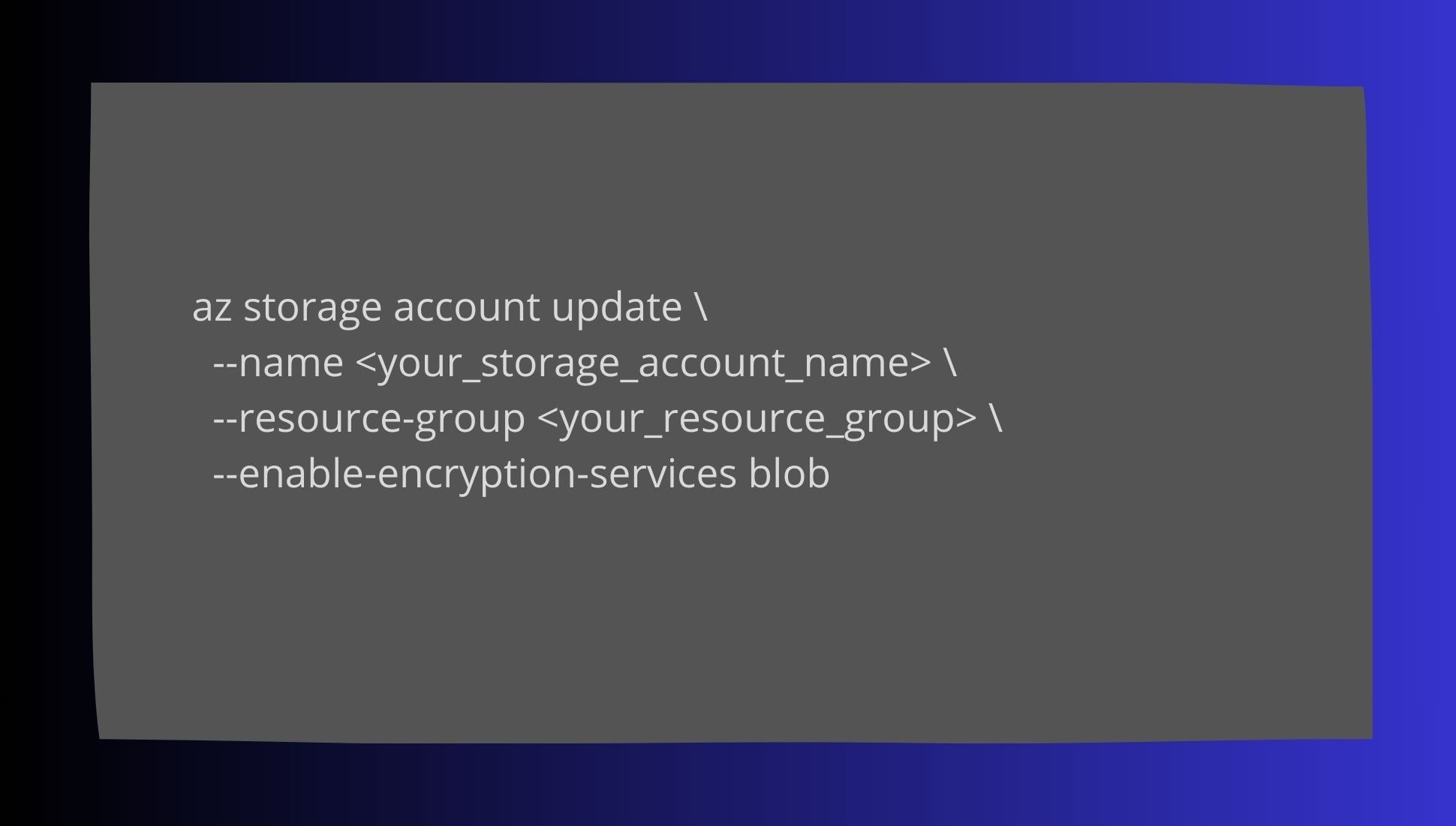
Azure Encryption for PHI: In Azure, enforce encryption for data stored in Azure Blob Storage by using Azure Storage Service Encryption (SSE):
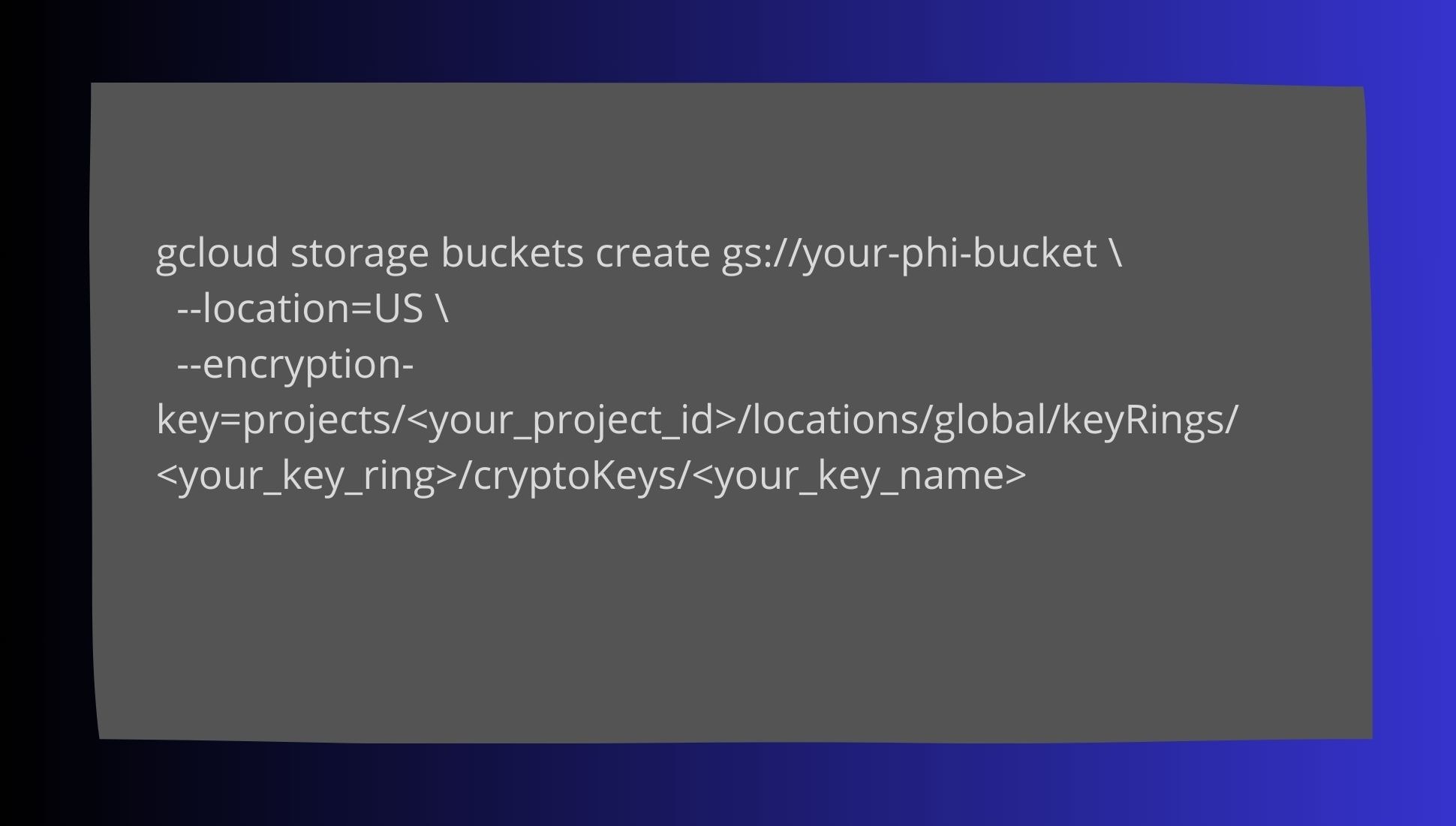
GCP Encryption for PHI: In Google Cloud, enable encryption using Customer-managed Encryption Keys (CMEK):
Automating Compliance Checks
Terraform for Infrastructure as Code (IaC): Terraform can help automate compliance checks in your DevOps pipeline. Here’s an example of setting up a secure S3 bucket:
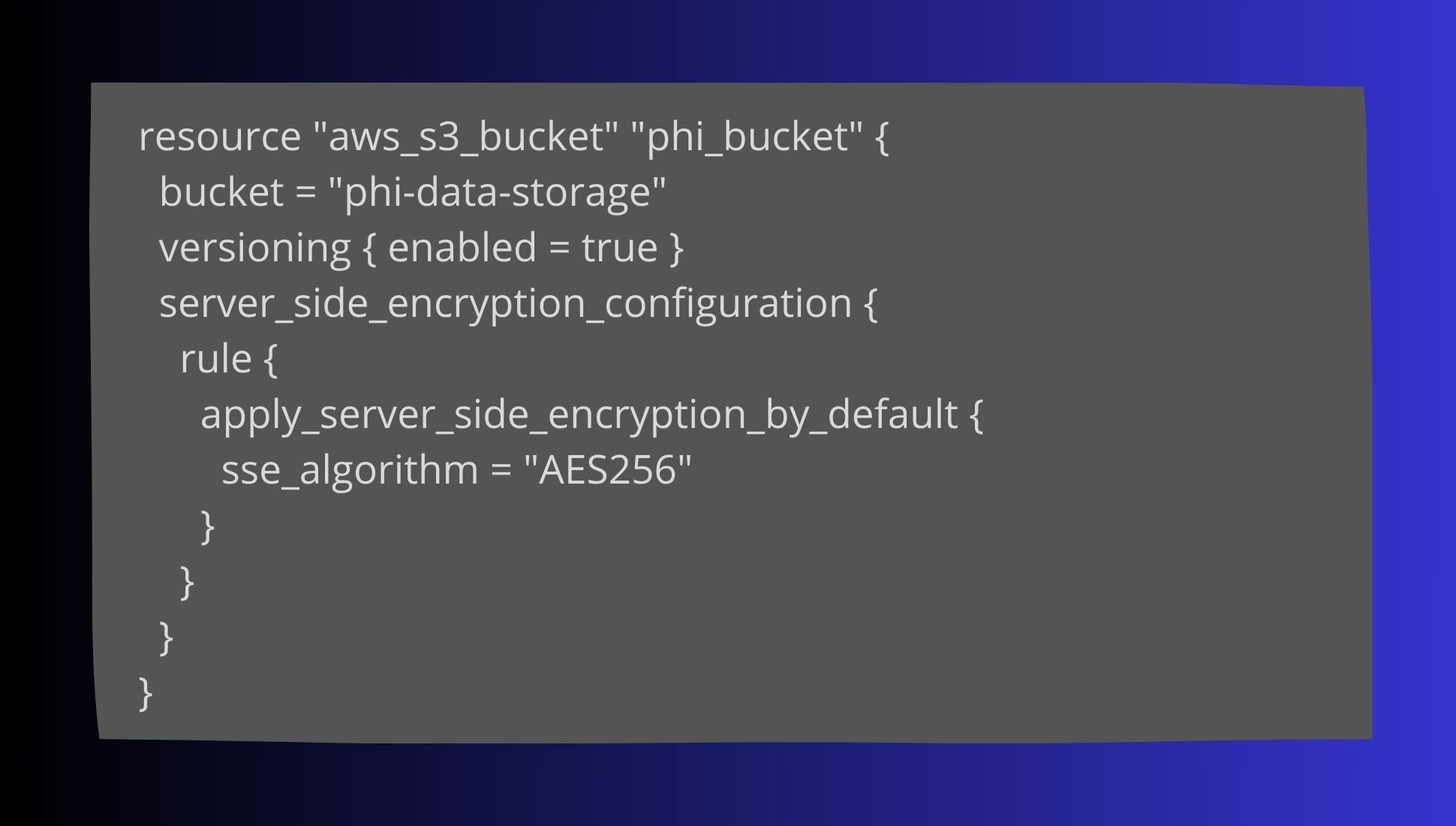
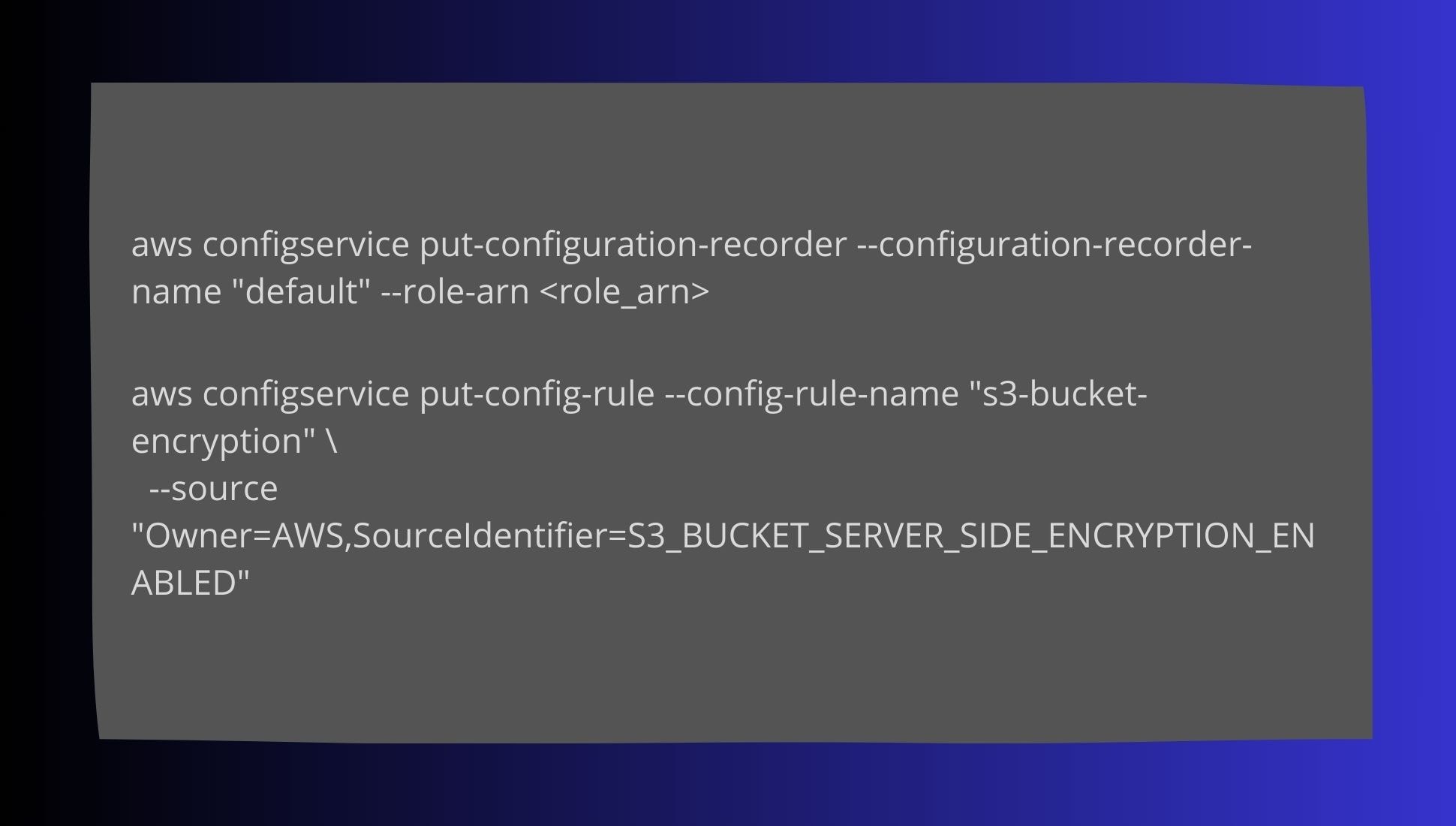
AWS Config for Monitoring Compliance: AWS Config continuously monitors your AWS resources for compliance. Set it up to ensure that S3 buckets meet HIPAA encryption requirements:
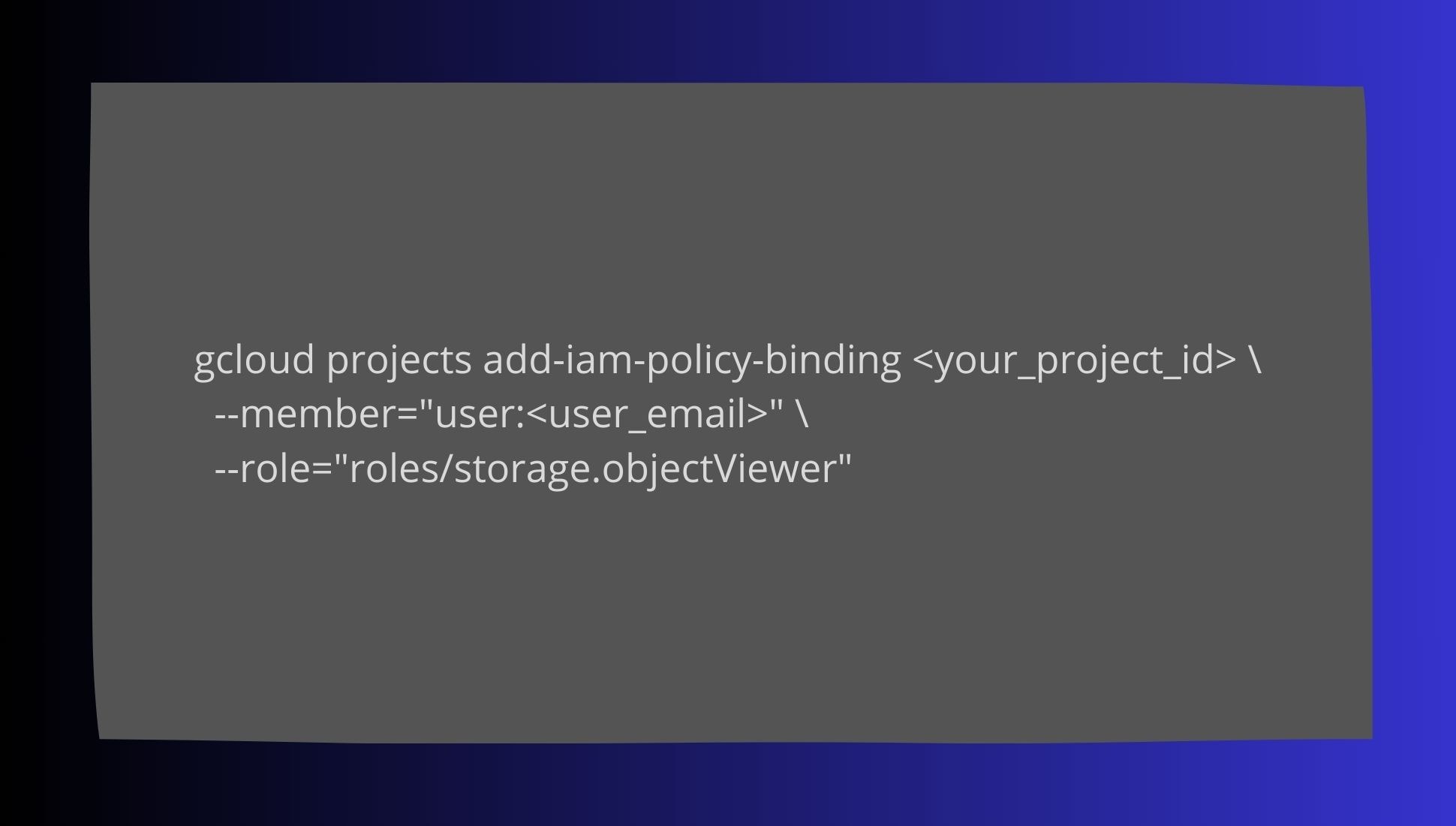
Role-Based Access Control (RBAC) Policies
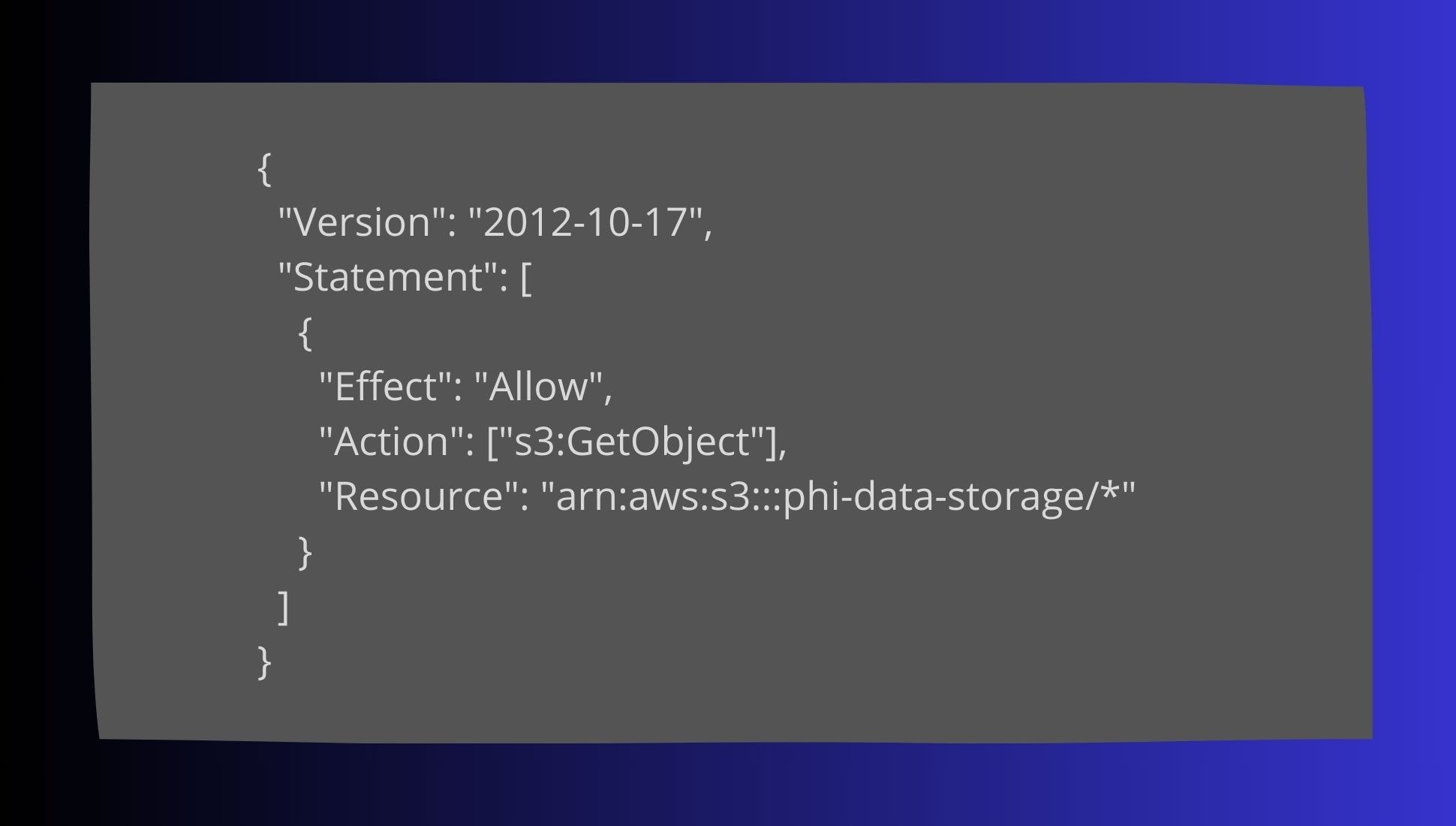
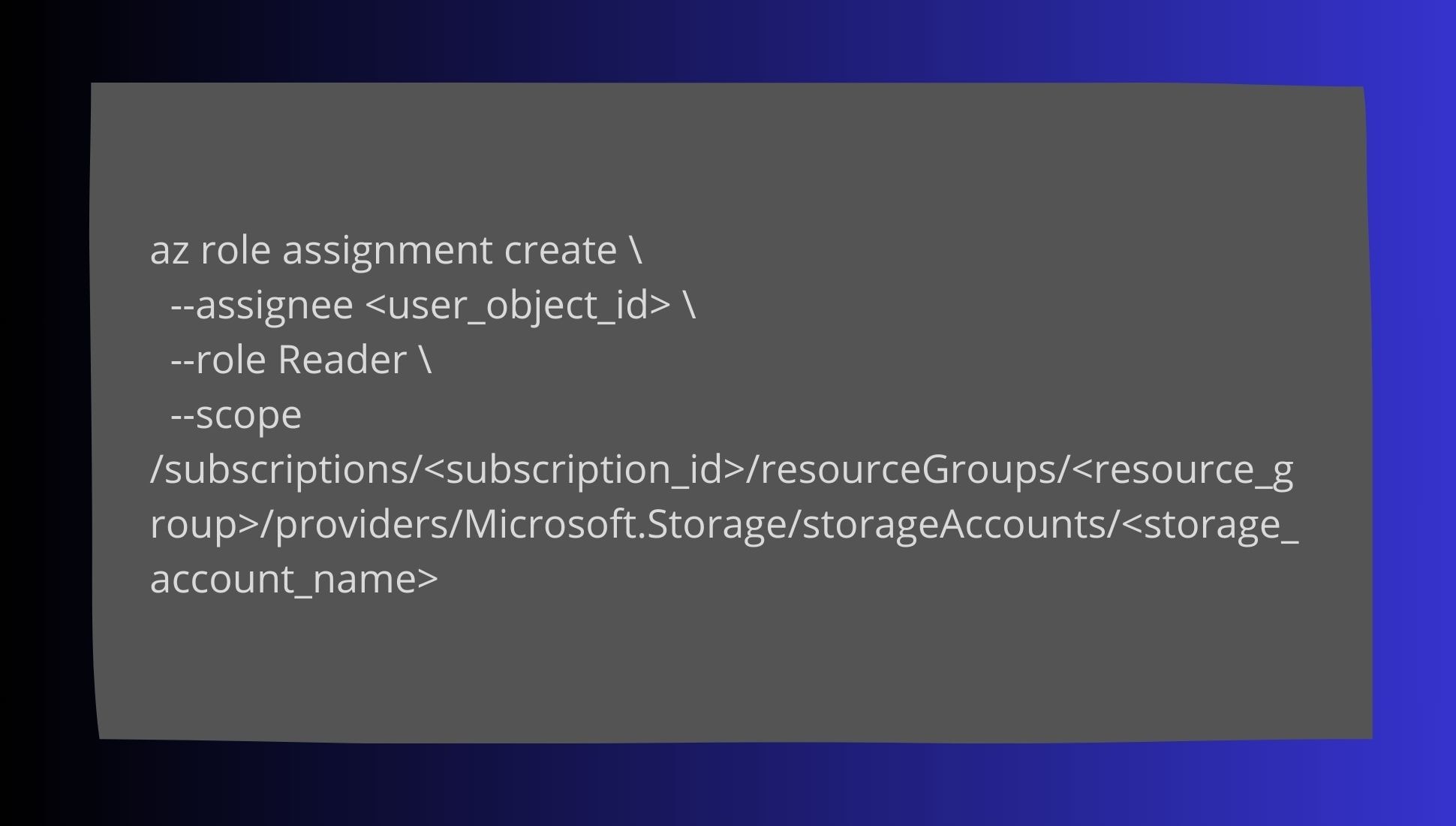
To ensure only authorized users can access PHI, implement RBAC policies. Here’s an example of RBAC in AWS, Azure, and GCP:
AWS RBAC Example:
Azure RBAC Example:
GCP RBAC Example:
To be HIPAA compliant and protect health data robustly DevOps teams need to integrate these encryption, compliance and access control into their workflows and create a secure and scalable cloud for health data.
DevOps Team Training and Awareness
A training program will get your DevOps team HIPAA confident. Here’s a 6 month training plan:
- Month 1: Introduction to HIPAA and PHI Learn about PHI and its impact on healthcare providers.
- Month 2: Cloud specific HIPAA Compliance Learn how AWS, Azure and GCP address HIPAA requirements.
- Month 3: Hands on Encryption and Access Control Implement encryption, RBAC and audit logging in cloud environments.
- Month 4: Breach Response Drills Simulate breach response scenarios, patient privacy and compliance.
- Month 5: Review and Update Security Policies Keep your security policies up to date with HIPAA changes.
- Month 6: Certification Prep for CISSP or CHP Prep team members for CISSP or CHP to increase security knowledge.
More Tools and Platforms for HIPAA Training:
- Cybrary: Has various HIPAA courses from beginner to advanced.
- AWS Training and Certification: Has training on cloud security and HIPAA compliance in AWS environments.
- KnowBe4: Has HIPAA compliance training and simulated phishing attacks to increase awareness.
- SANS Institute: Has courses on HIPAA compliance and security best practices.
- HIPAA Academy: Has free resources and certification for HIPAA professionals.
By following this training plan your DevOps team will be HIPAA confident. And consistent reinforcement of HIPAA principles – whether through simulated drills, updates on best practices or certification prep – will make compliance a part of your organization’s DNA.
Violating HIPAA Privacy Rule Consequences
- Fines: $100 to $1.5 million per violation depending on the severity.
- Legal: 10 years in prison for severe violations, especially intentional misuse of PHI.
- Reputation: A single breach can destroy customer trust and break business partnerships.
- Breach Notification: Under HIPAA’s Breach Notification Rule any unauthorized disclosure of PHI must be reported to the individual, HHS and in some cases the media.
- Regulatory Scrutiny: The OCR enforces HIPAA and a history of violations will bring audits, legal action and more restrictions on how you handle health data.
Baking HIPAA into Your DevOps
To be HIPAA compliant you need to review your policies regularly. HIPAA laws like the HIPAA Privacy Rule and HIPAA Security Rule are updated as new technologies and threats emerge. Compliance isn’t a one time task – it’s an ongoing process. Teams should review their breach response plans, patient’s health information protection and cloud security configurations regularly to ensure they are in line with the national standards.
Having a security focused DevOps culture – often called DevSecOps – is key to HIPAA compliance. DevSecOps is about embedding security into every phase of development from planning to deployment so compliance is part of the workflow. This proactive approach prevents vulnerabilities and ensures patients health information is confidential and intact.
DevSecOps includes automatic compliance checks, so your team can monitor for security gaps that could lead to HIPAA violations. Automation tools that test for non-compliant configurations can be added to the CI/CD pipeline to reduce human error and speed up response time when compliance issues occur. And audit logs must be reviewed continuously to ensure only the right information is being accessed by the right people.
Training staff is another key piece. From developers to project managers everyone in the workflow needs to know their role in protecting health data. By having a strong HIPAA culture, organizations create an environment where compliance is top of mind and individually identifiable health information is respected throughout the project lifecycle.
Conclusion
HIPAA compliance doesn’t have to be painful. By integrating security into your DevOps and cloud migration from the outset, compliance will become second nature. A-Dev can guide your team through these challenges, ensuring your cloud infrastructure is both scalable and secure.
Make HIPAA training a core part of your workflow, not an afterthought. Protect your data, avoid fines, and build trust with your healthcare partners. Contact A-Dev today.





